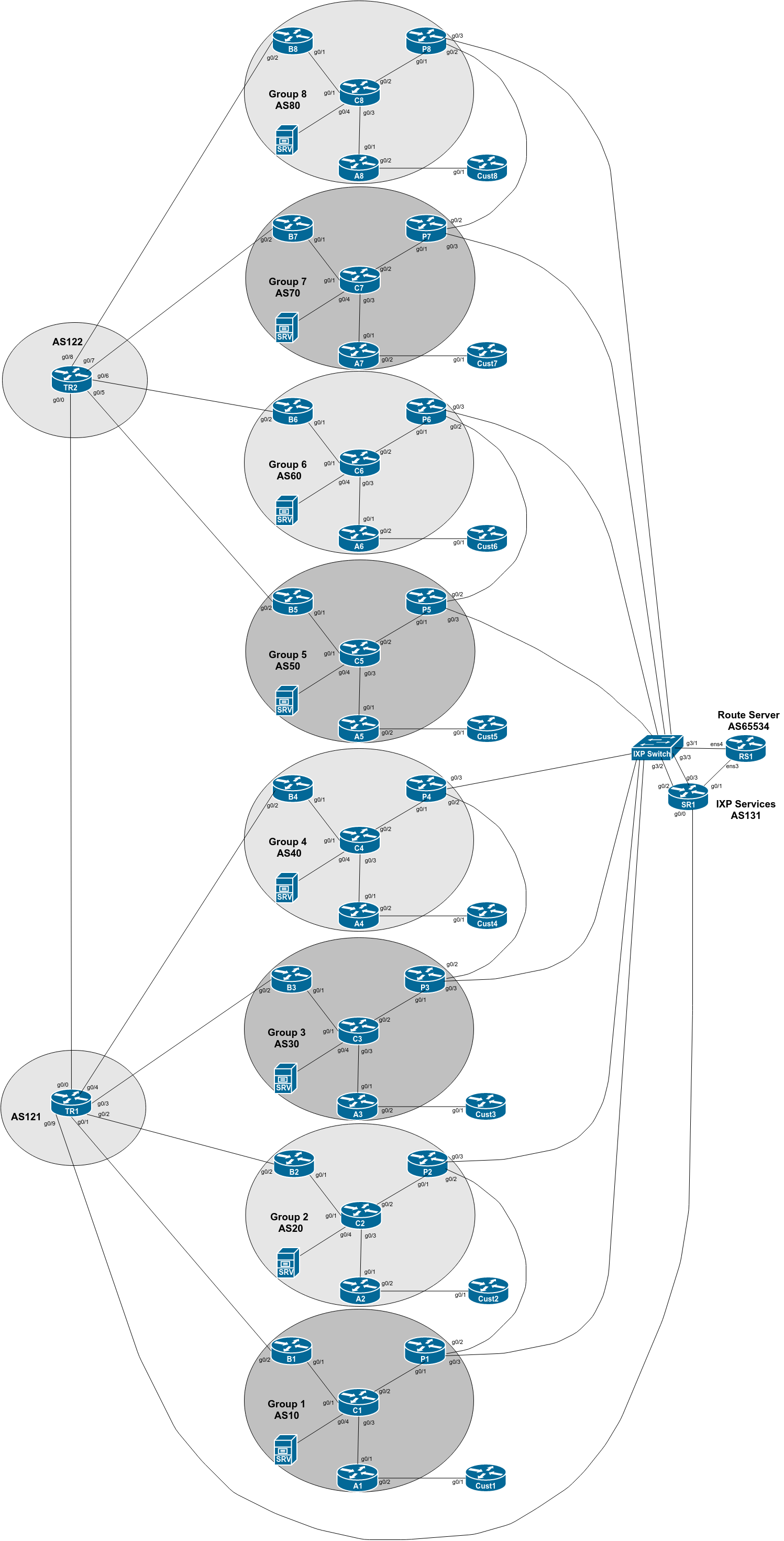
The purpose of this part of the lab is introduce an Internet Exchange Point into our lab. IXPs are a very important if not critical component of today’s Internet architecture, and it is vitally important to ensure the correct configuration so that network operators gain maximum advantage from their participation at an IXP.
The lab topology has been further enhanced according to the diagram below.

We have introduced an Internet Exchange Point for each group to connect to. The IXP also has a Route Server and a Services Router; the latter is used to give transit to any of the services that the IXP might be offering to its members (eg DNS, content caching, NTP, Looking Glass, etc). We will set this up later on in this lab.
Each group should now configure their link to the IXP according to the above diagram.
Consult the IP Address Plan document for the address space used by the IXP. Following the document, configure the interface on the Peering router accordingly.
interface GigabitEthernet 0/3
description ASX0 link to IXP
ip address 100.127.1.X 255.255.255.0
no ip directed-broadcast
no ip redirects
no ip proxy-arp
ipv6 address 2001:DB8:FFFF:1::X/64
ipv6 nd prefix default no-advertise
ipv6 nd ra suppress all
no shutdown
!Note the subnet masks - this time the ethernet is NOT a point-to-point link but a shared LAN media. Once the interfaces have been configured, see if you can ping any of the other groups on their IXP addresses (both IPv4 and IPv6). Are you able to ping the Route Server too?
Do not configure IS-IS towards any IXP peer! They are not part of your autonomous system.
However, so that traceroutes across the IXP do not break, we might wish to carry the IXP LAN address block within our IS-IS (not iBGP). To do this, we simply mark the IXP facing interface as passive in the IS-IS configuration. Here is an example:
router isis asX0
passive-interface GigabitEthernet 0/3If you recall from the IS-IS presentation, this will tell IS-IS to announce the subnet attached to this interface.
Now all routers in your AS will see the IXP LAN address - check from your Core, Access and Border routers, just to make sure.
In earlier labs, we attached a specific community to each type of route we introduced into our IBGP. We are going to do the same thing for the routes we learn from our private peers, as the following sections show.
This is the community we will be using:
| Prefix Type | Community | Description |
|---|---|---|
| IXP RS Peer addresses | AS:1300 | Any addresses our IXP RS peers send to us |
Each group now needs to add one more community definition on their Border, Core, Peering and Access routers (not the Customer router, which is not in the group’s AS).
ip community-list standard RS-peer permit X0:1300
We now configure eBGP on our Peering Router with the Exchange Point’s Route Server (we will add in bi-lateral BGP peering in a later lab, but for now we will just peer with the Route Server).
The Route Server sits in AS 65534 - this is a private AS, and is not visible on the public Internet. In fact, we don’t want this AS to be visible inside our own AS either, and that’s one of the unique features of a Route Server1 - it does not add its AS into the AS path when distributing prefixes to its eBGP neighbours.
DO NOT forget to filter what you hear from the Route Server, and what you send to the Route Server. You should only accept the address blocks originated by the other IXP participants (they may send you more by mistake!), and you should only send prefixes you originate!
First let’s implement the route-map which looks for our aggregate being tagged by the “aggregate” community (and customer-pi too), and only sends that. It’s similar to the one we created for our private peer in the previous lab:
route-map IXP-RS-out permit 5
description Prefixes to our IXP Peers
match community aggregate
match community customer-pi
!Note that the same route-map can be used for both IPv4 and IPv6 as it only matches against the BGP community values.
For our inbound policy configuration, we are going to use a route-map from the outset as that will give us greater policy flexibility as we proceed through the remaining labs.
Now we need to set up inbound filters for the prefixes we expect to hear from the Route Server. Add a line for each group that we expect to hear from the Route Server.
Note carefully: Group 1 will only expect to hear prefixes from Groups 2 through 8; Group 2 will only expect to hear prefixes from Groups 1, 3 to 7, etc. Don’t be lazy and accept your own prefix from any IXP peer.
IPv4 example:
ip prefix-list IXP-RS description IPv4 Prefixes from Route-Server
ip prefix-list IXP-RS permit 100.68.<first-group>.0/24
..etc..IPv6 Example:
ipv6 prefix-list IXP-v6RS description IPv6 Prefixes from Route-Server
ipv6 prefix-list IXP-v6RS permit 2001:DB8:<first-group>::/48
..etc..Once complete, each prefix list should have 7 entries in them.
And then we create a route-map to apply the prefix-list. First for IPv4:
route-map IXP-RS-in permit 5
description Filter and tag prefixes from IXP RS
match ip address prefix-list IXP-RS
set community X0:1300
!And for IPv6:
route-map IXP-RSv6-in permit 5
description Filter and tag prefixes from IXP RS
match ipv6 address prefix-list IXP-v6RS
set community X0:1300
!Notice we have to use different route-maps for IPv4 and IPv6 as they have address-family specific configuration (prefix-lists) in them.
Finally we apply the newly created inbound and outbound policies. Here is a configuration sample - note that we are reusing some configuration we have set up earlier:
router bgp X0
address-family ipv4
neighbor 100.127.1.254 remote-as 65534
neighbor 100.127.1.254 description eBGP with IXP RS
neighbor 100.127.1.254 password ixp-rs
neighbor 100.127.1.254 route-map IXP-RS-out out
neighbor 100.127.1.254 route-map IXP-RS-in in
neighbor 100.127.1.254 activate
!
address-family ipv6
neighbor 2001:DB8:FFFF:1::FE remote-as 65534
neighbor 2001:DB8:FFFF:1::FE description eBGP with IXP RS
neighbor 2001:DB8:FFFF:1::FE password ixp-rs
neighbor 2001:DB8:FFFF:1::FE route-map IXP-RS-out out
neighbor 2001:DB8:FFFF:1::FE route-map IXP-RSv6-in in
neighbor 2001:DB8:FFFF:1::FE activate
!Once this has been configured, has the BGP session with the Route Server established? If not, why not? What do the router logs tell you?
You will notice from the logs that the router is complaining about a BGP peer AS not being in the announced AS path - this is Cisco IOS protecting against improper BGP announcements because, according to the BGP RFC, the AS number of the neighbouring AS must appear as the adjacent AS in the AS PATH. And if you recall from early on in the notes, that was a special feature of the Route Server: its AS does not appear in the path.
So we need to turn this safety check off in IOS:
router bgp X0
no bgp enforce-first-asand once this has been done you will now see that the eBGP sessions with the Route Server will have been established.
Now that the BGP session with the Route Server is fully established, what do you now see in the BGP table?
What about the routes between you and your private peer that you set up earlier? Which is the best path now? Through the IXP, or over the private peering link?
Explain what you see to the workshop instructors. What can we do about this2?
You will have noticed from the IXP diagram that the IXP has services it offers to the participant members. These are usually the IXP website, DNS gTLD and ccTLD, usually a root name server instance, and perhaps even a CDN Cache or two. These services need transit to reach the Internet - this transit is not provided through the IXP, but via a separate transit connection that the IXP membership purchases from a transit provider (or two).
In our example, the IXP is buying transit from AS121, and so has a direct connection to TR1 router.
The workshop instructors will now enable the link from the IXP’s services router to AS121’s TR router.
You should now notice the address space used by the IXP’s services infrastructure appearing in the routing table within your group. Consult the IP Address Plan document for the address space used by the IXP and see if this is what you now see in your BGP table.
What does your BGP table show?
Check on your Border and Peering Routers.
You will have noticed that your Border router will have received the IXP’s IPv4 and IPv6 Services address blocks from the upstream transit provider. This is because the upstream is sending all routes to you.
However, the IXP Services should also be visible across the Internet Exchange Point - after all, each Group is a member of the IX! And it is more efficient, lower latency, lower cost, than sending traffic via the transit provider.
We need to update our inbound filters for the Route Server peering to include the IXP’s Services address space. Let’s go back to the prefix-lists and add the extra lines in:
ip prefix-list IXP-RS permit 100.127.0.0/24and
ipv6 prefix-list IXP-v6RS permit 2001:DB8:FFFF::/48Once the filters have been updated, do an inbound route-refresh on the peering with the Router Server.
What do you seen your BGP table now?
Compare what the Border Router has in its table with what the Peering Router has in its table.
Which is the best path?
This appendix shows the configuration of the route server as used for this workshop. It uses BIRD, the most commonly use Route Server software at Internet Exchange Points today3. BIRD runs on a variety of Linux operating systems - we use Ubuntu 18.04 LTS for these workshops.
# This configuration based on:
# https://gitlab.labs.nic.cz/labs/bird/-/wikis/Simple_route_server
# https://gitlab.labs.nic.cz/labs/bird/-/wikis/transition-notes-to-bird-2
# https://github.com/pierky/arouteserver/blob/master/examples/default/bird_v2.conf
#
# For more options see:
# /usr/share/doc/bird2/examples/bird.conf
# https://bird.network.cz/?get_doc&f=bird.html&v=20
log "/var/log/bird/bird.log" all;
#log syslog all;
router id 100.127.1.254;
define myas = 65534;
protocol device { }
# This function returns True if 'net' is a bogon prefix
# or falls within a bogon prefix.
function prefix_is_bogon()
prefix set bogons_4;
prefix set bogons_6;
{
bogons_4 = [
# Default route
0.0.0.0/0,
# IANA - Local Identification
0.0.0.0/8{8,32},
# RFC 1918 - Private Use
10.0.0.0/8{8,32},
# IANA - Loopback
127.0.0.0/8{8,32},
# RFC 6598 - Shared Address Space
# NSRC: commented out as we use this
# 100.64.0.0/10{10,32},
# RFC 3927 - Link Local
169.254.0.0/16{16,32},
# RFC 1918 - Private Use
172.16.0.0/12{12,32},
# RFC 5737 - TEST-NET-1
192.0.2.0/24{24,32},
# RFC 3068 - 6to4 prefix
192.88.99.0/24{24,32},
# RFC 1918 - Private Use
192.168.0.0/16{16,32},
# RFC 2544 - Network Interconnect Device Benchmark Testing
198.18.0.0/15{15,32},
# RFC 5737 - TEST-NET-2
198.51.100.0/24{24,32},
# RFC 5737 - TEST-NET-3
203.0.113.0/24{24,32},
# RFC 5771 - Multicast (formerly Class D) and Class E
224.0.0.0/3{3,32}
];
bogons_6 = [
# Default route
::/0,
# loopback, unspecified, v4-mapped
::/8{8,128},
# RFC 6052 - IPv4-IPv6 Translation
64:ff9b::/96{96,128},
# RFC 6666 - reserved for Discard-Only Address Block
100::/8{8,128},
# RFC 4048 - Reserved by IETF
200::/7{7,128},
# RFC 4291 - Reserved by IETF
400::/6{6,128},
# RFC 4291 - Reserved by IETF
800::/5{5,128},
# RFC 4291 - Reserved by IETF
1000::/4{4,128},
# RFC 4380 - Teredo prefix
2001::/32{32,128},
# RFC 5180 - Benchmarking
2001:2::/48{48,128},
# RFC 7450 - Automatic Multicast Tunneling
2001:3::/32{32,128},
# RFC 4843 - Deprecated ORCHID
# NSRC: commented out as we use 2001:18::/31
# 2001:10::/28{28,128},
# RFC 7343 - ORCHIDv2
2001:20::/28{28,128},
# RFC 3849 - NON-ROUTABLE range to be used for documentation purpose
# NSRC: commented out as we use it
# 2001:db8::/32{32,128},
# RFC 3068 - 6to4 prefix
2002::/16{16,128},
# RFC 5156 - used for the 6bone but was returned
3ffe::/16{16,128},
# RFC 4291 - Reserved by IETF
4000::/2{2,128},
# RFC 4291 - Reserved by IETF
8000::/1{1,128}
];
if net.type = NET_IP4 then
if net ~ bogons_4 then return true;
if net.type = NET_IP6 then
if net ~ bogons_6 then return true;
return false;
}
####
# Protocol template
template bgp PEERS {
local as myas;
rs client;
}
####
# Configuration of BGP peer follows
###
filter bgp_in_AS131
prefix set allnet;
int set allas;
{
if (prefix_is_bogon()) then reject;
if (bgp_path.first != 131 ) then reject;
allas = [ 131 ];
if ! (bgp_path.last ~ allas) then reject;
allnet = [ 100.127.0.0/24, 2001:DB8:FFFF::/48 ];
if ! (net ~ allnet) then reject;
accept;
}
protocol bgp SR1v4 from PEERS {
description "SR1 - IPv4";
neighbor 100.127.1.253 as 131;
password "ixp-rs";
ipv4 {
import filter bgp_in_AS131;
import limit 10000 action restart;
export all;
};
}
protocol bgp SR1v6 from PEERS {
description "SR1 - IPv6";
neighbor 2001:DB8:FFFF:1::FD as 131;
password "ixp-rs";
ipv6 {
import filter bgp_in_AS131;
import limit 10000 action restart;
export all;
};
}
### AS10 - Group 1
filter bgp_in_AS10
prefix set allnet;
int set allas;
{
if (prefix_is_bogon()) then reject;
if (bgp_path.first != 10 ) then reject;
allas = [ 10, 100010, 100020 ];
if ! (bgp_path.last ~ allas) then reject;
allnet = [ 100.68.1.0/24, 100.68.101.0/24, 100.68.102.0/24,
2001:DB8:1::/48, 2001:DB8:101::/48, 2001:DB8:102::/48 ];
if ! (net ~ allnet) then reject;
accept;
}
protocol bgp R10v4 from PEERS {
description "Group 1 - IPv4";
neighbor 100.127.1.1 as 10;
password "ixp-rs";
ipv4 {
import filter bgp_in_AS10;
import limit 10000 action restart;
export all;
};
}
protocol bgp R10v6 from PEERS {
description "Group 1 - IPv6";
neighbor 2001:DB8:FFFF:1::1 as 10;
password "ixp-rs";
ipv6 {
import filter bgp_in_AS10;
import limit 10000 action restart;
export all;
};
}
### AS20 - Group 2
filter bgp_in_AS20
prefix set allnet;
int set allas;
{
if (prefix_is_bogon()) then reject;
if (bgp_path.first != 20 ) then reject;
allas = [ 20, 100020, 100010 ];
if ! (bgp_path.last ~ allas) then reject;
allnet = [ 100.68.2.0/24, 100.68.102.0/24, 100.68.101.0/24,
2001:DB8:2::/48, 2001:DB8:102::/48, 2001:DB8:101::/48 ];
if ! (net ~ allnet) then reject;
accept;
}
protocol bgp R20v4 from PEERS {
description "Group 2 - IPv4";
neighbor 100.127.1.2 as 20;
password "ixp-rs";
ipv4 {
import filter bgp_in_AS20;
import limit 10000 action restart;
export all;
};
}
protocol bgp R20v6 from PEERS {
description "Group 2 - IPv6";
neighbor 2001:DB8:FFFF:1::2 as 20;
password "ixp-rs";
ipv6 {
import filter bgp_in_AS20;
import limit 10000 action restart;
export all;
};
}
### AS30 - Group 3
filter bgp_in_AS30
prefix set allnet;
int set allas;
{
if (prefix_is_bogon()) then reject;
if (bgp_path.first != 30 ) then reject;
allas = [ 30, 100030, 100040 ];
if ! (bgp_path.last ~ allas) then reject;
allnet = [ 100.68.3.0/24, 100.68.103.0/24, 100.68.104.0/24,
2001:DB8:3::/48, 2001:DB8:103::/48, 2001:DB8:104::/48 ];
if ! (net ~ allnet) then reject;
accept;
}
protocol bgp R30v4 from PEERS {
description "Group 3 - IPv4";
neighbor 100.127.1.3 as 30;
password "ixp-rs";
ipv4 {
import filter bgp_in_AS30;
import limit 10000 action restart;
export all;
};
}
protocol bgp R30v6 from PEERS {
description "Group 3 - IPv6";
neighbor 2001:DB8:FFFF:1::3 as 30;
password "ixp-rs";
ipv6 {
import filter bgp_in_AS30;
import limit 10000 action restart;
export all;
};
}
### AS40 - Group 4
filter bgp_in_AS40
prefix set allnet;
int set allas;
{
if (prefix_is_bogon()) then reject;
if (bgp_path.first != 40 ) then reject;
allas = [ 40, 100040, 100030 ];
if ! (bgp_path.last ~ allas) then reject;
allnet = [ 100.68.4.0/24, 100.68.104.0/24, 100.68.103.0/24,
2001:DB8:4::/48, 2001:DB8:104::/48, 2001:DB8:103::/48 ];
if ! (net ~ allnet) then reject;
accept;
}
protocol bgp R40v4 from PEERS {
description "Group 4 - IPv4";
neighbor 100.127.1.4 as 40;
password "ixp-rs";
ipv4 {
import filter bgp_in_AS40;
import limit 10000 action restart;
export all;
};
}
protocol bgp R40v6 from PEERS {
description "Group 4 - IPv6";
neighbor 2001:DB8:FFFF:1::4 as 40;
password "ixp-rs";
ipv6 {
import filter bgp_in_AS40;
import limit 10000 action restart;
export all;
};
}
### AS50 - Group 5
filter bgp_in_AS50
prefix set allnet;
int set allas;
{
if (prefix_is_bogon()) then reject;
if (bgp_path.first != 50 ) then reject;
allas = [ 50, 100050, 100060 ];
if ! (bgp_path.last ~ allas) then reject;
allnet = [ 100.68.5.0/24, 100.68.105.0/24, 100.68.106.0/24,
2001:DB8:5::/48, 2001:DB8:105::/48, 2001:DB8:106::/48 ];
if ! (net ~ allnet) then reject;
accept;
}
protocol bgp R50v4 from PEERS {
description "Group 5 - IPv4";
neighbor 100.127.1.5 as 50;
password "ixp-rs";
ipv4 {
import filter bgp_in_AS50;
import limit 10000 action restart;
export all;
};
}
protocol bgp R50v6 from PEERS {
description "Group 5 - IPv6";
neighbor 2001:DB8:FFFF:1::5 as 50;
password "ixp-rs";
ipv6 {
import filter bgp_in_AS50;
import limit 10000 action restart;
export all;
};
}
### AS60 - Group 6
filter bgp_in_AS60
prefix set allnet;
int set allas;
{
if (prefix_is_bogon()) then reject;
if (bgp_path.first != 60 ) then reject;
allas = [ 60, 100060, 100050 ];
if ! (bgp_path.last ~ allas) then reject;
allnet = [ 100.68.6.0/24, 100.68.106.0/24, 100.68.105.0/24,
2001:DB8:6::/48, 2001:DB8:106::/48, 2001:DB8:105::/48 ];
if ! (net ~ allnet) then reject;
accept;
}
protocol bgp R60v4 from PEERS {
description "Group 6 - IPv4";
neighbor 100.127.1.6 as 60;
password "ixp-rs";
ipv4 {
import filter bgp_in_AS60;
import limit 10000 action restart;
export all;
};
}
protocol bgp R60v6 from PEERS {
description "Group 6 - IPv6";
neighbor 2001:DB8:FFFF:1::6 as 60;
password "ixp-rs";
ipv6 {
import filter bgp_in_AS60;
import limit 10000 action restart;
export all;
};
}
### AS70 - Group 7
filter bgp_in_AS70
prefix set allnet;
int set allas;
{
if (prefix_is_bogon()) then reject;
if (bgp_path.first != 70 ) then reject;
allas = [ 70, 100070, 100080 ];
if ! (bgp_path.last ~ allas) then reject;
allnet = [ 100.68.7.0/24, 100.68.107.0/24, 100.68.108.0/24,
2001:DB8:7::/48, 2001:DB8:107::/48, 2001:DB8:108::/48 ];
if ! (net ~ allnet) then reject;
accept;
}
protocol bgp R70v4 from PEERS {
description "Group 7 - IPv4";
neighbor 100.127.1.7 as 70;
password "ixp-rs";
ipv4 {
import filter bgp_in_AS70;
import limit 10000 action restart;
export all;
};
}
protocol bgp R70v6 from PEERS {
description "Group 7 - IPv6";
neighbor 2001:DB8:FFFF:1::7 as 70;
password "ixp-rs";
ipv6 {
import filter bgp_in_AS70;
import limit 10000 action restart;
export all;
};
}
### AS80 - Group 8
filter bgp_in_AS80
prefix set allnet;
int set allas;
{
if (prefix_is_bogon()) then reject;
if (bgp_path.first != 80 ) then reject;
allas = [ 80, 100080, 100070 ];
if ! (bgp_path.last ~ allas) then reject;
allnet = [ 100.68.8.0/24, 100.68.108.0/24, 100.68.107.0/24,
2001:DB8:8::/48, 2001:DB8:108::/48, 2001:DB8:107::/48 ];
if ! (net ~ allnet) then reject;
accept;
}
protocol bgp R80v4 from PEERS {
description "Group 8 - IPv4";
neighbor 100.127.1.8 as 80;
password "ixp-rs";
ipv4 {
import filter bgp_in_AS80;
import limit 10000 action restart;
export all;
};
}
protocol bgp R80v6 from PEERS {
description "Group 8 - IPv6";
neighbor 2001:DB8:FFFF:1::8 as 80;
password "ixp-rs";
ipv6 {
import filter bgp_in_AS80;
import limit 10000 action restart;
export all;
};
}
This appendix shows the configuration of the route server used for older versions of this workshop. It is Cisco IOS based - in the mid 2000s Cisco had a project to produce a route server implementation in IOS, but it lacked traction amongst IXPs and showed relatively poor performance when compared with Open Source implementations such as BIRD. However, the code remains in IOS/IOS-XE on the higher end platforms.
interface GigabitEthernet0/0
description IXP LAN
ip address 100.127.1.254 255.255.255.0
no ip redirects
no ip proxy-arp
ipv6 address 2001:DB8:FFFF:1::FE/64
ipv6 nd prefix default no-advertise
ipv6 nd ra suppress all
!
router bgp 65534
bgp log-neighbor-changes
bgp deterministic-med
no bgp default ipv4-unicast
neighbor ixp-peers peer-group
neighbor ixp-peers password ixp-rs
neighbor v6ixp-peers peer-group
neighbor v6ixp-peers password ixp-rs
neighbor 100.127.1.1 remote-as 10
neighbor 100.127.1.1 peer-group ixp-peers
neighbor 100.127.1.1 description AS10 peer
neighbor 100.127.1.2 remote-as 20
neighbor 100.127.1.2 peer-group ixp-peers
neighbor 100.127.1.2 description AS20 peer
neighbor 100.127.1.3 remote-as 30
neighbor 100.127.1.3 peer-group ixp-peers
neighbor 100.127.1.3 description AS30 peer
neighbor 100.127.1.4 remote-as 40
neighbor 100.127.1.4 peer-group ixp-peers
neighbor 100.127.1.4 description AS40 peer
neighbor 100.127.1.5 remote-as 50
neighbor 100.127.1.5 peer-group ixp-peers
neighbor 100.127.1.5 description AS50 peer
neighbor 100.127.1.6 remote-as 60
neighbor 100.127.1.6 peer-group ixp-peers
neighbor 100.127.1.6 description AS60 peer
neighbor 100.127.1.7 remote-as 70
neighbor 100.127.1.7 peer-group ixp-peers
neighbor 100.127.1.7 description AS70 peer
neighbor 100.127.1.8 remote-as 80
neighbor 100.127.1.8 peer-group ixp-peers
neighbor 100.127.1.8 description AS80 peer
neighbor 100.127.1.253 remote-as 131
neighbor 100.127.1.253 peer-group ixp-peers
neighbor 100.127.1.253 description IXP Services
neighbor 2001:DB8:FFFF:1::1 remote-as 10
neighbor 2001:DB8:FFFF:1::1 peer-group v6ixp-peers
neighbor 2001:DB8:FFFF:1::1 description AS10 peer
neighbor 2001:DB8:FFFF:1::2 remote-as 20
neighbor 2001:DB8:FFFF:1::2 peer-group v6ixp-peers
neighbor 2001:DB8:FFFF:1::2 description AS20 peer
neighbor 2001:DB8:FFFF:1::3 remote-as 30
neighbor 2001:DB8:FFFF:1::3 peer-group v6ixp-peers
neighbor 2001:DB8:FFFF:1::3 description AS30 peer
neighbor 2001:DB8:FFFF:1::4 remote-as 40
neighbor 2001:DB8:FFFF:1::4 peer-group v6ixp-peers
neighbor 2001:DB8:FFFF:1::4 description AS40 peer
neighbor 2001:DB8:FFFF:1::5 remote-as 50
neighbor 2001:DB8:FFFF:1::5 peer-group v6ixp-peers
neighbor 2001:DB8:FFFF:1::5 description AS50 peer
neighbor 2001:DB8:FFFF:1::6 remote-as 60
neighbor 2001:DB8:FFFF:1::6 peer-group v6ixp-peers
neighbor 2001:DB8:FFFF:1::6 description AS60 peer
neighbor 2001:DB8:FFFF:1::7 remote-as 70
neighbor 2001:DB8:FFFF:1::7 peer-group v6ixp-peers
neighbor 2001:DB8:FFFF:1::7 description AS70 peer
neighbor 2001:DB8:FFFF:1::8 remote-as 80
neighbor 2001:DB8:FFFF:1::8 peer-group v6ixp-peers
neighbor 2001:DB8:FFFF:1::8 description AS80 peer
neighbor 2001:DB8:FFFF:1::FD remote-as 131
neighbor 2001:DB8:FFFF:1::FD peer-group v6ixp-peers
neighbor 2001:DB8:FFFF:1::FD description IXP Services
!
address-family ipv4
neighbor ixp-peers route-server-client
neighbor 100.127.1.1 activate
neighbor 100.127.1.2 activate
neighbor 100.127.1.3 activate
neighbor 100.127.1.4 activate
neighbor 100.127.1.5 activate
neighbor 100.127.1.6 activate
neighbor 100.127.1.7 activate
neighbor 100.127.1.8 activate
neighbor 100.127.1.253 activate
distance bgp 200 200 200
exit-address-family
!
address-family ipv6
neighbor v6ixp-peers route-server-client
neighbor 2001:DB8:FFFF:1::1 activate
neighbor 2001:DB8:FFFF:1::2 activate
neighbor 2001:DB8:FFFF:1::3 activate
neighbor 2001:DB8:FFFF:1::4 activate
neighbor 2001:DB8:FFFF:1::5 activate
neighbor 2001:DB8:FFFF:1::6 activate
neighbor 2001:DB8:FFFF:1::7 activate
neighbor 2001:DB8:FFFF:1::8 activate
neighbor 2001:DB8:FFFF:1::FD activate
distance bgp 200 200 200
exit-address-family
!
ip route 0.0.0.0 0.0.0.0 Null0
!
ipv6 route ::/0 Null0
!
See RFC7948 for a complete and detailed description of how a Route Server operates and can be used at an Internet Exchange Point.↩
Cisco IOS BGP Best Path Selection process includes a step which chooses the oldest path stored in the BGP table. So we are seeing the results of this. We brought up the Private Peering first, and the IXP Peering after that. So the router prefers the Private Peering. Shutting down and then bringing up the private peering again will result in the best path between the adjacent ASNs going over the IXP. It’s a not deterministic, which is a problem. You can disable this in IOS by adding in the bgp bestpath compare-routerid configuration under the BGP process - then the router will not compare the age of the prefixes heard, but compare the router-id’s of the neighbours which sent the prefix.↩
The most popular Route Server software today is BIRD, used by most IXPs worldwide. The LINX modified version of Quagga is also used (Quagga itself is not scalable and can only handle a few neighbours). And GoBGP is also another Route Server candidate being used by some IXPs.↩