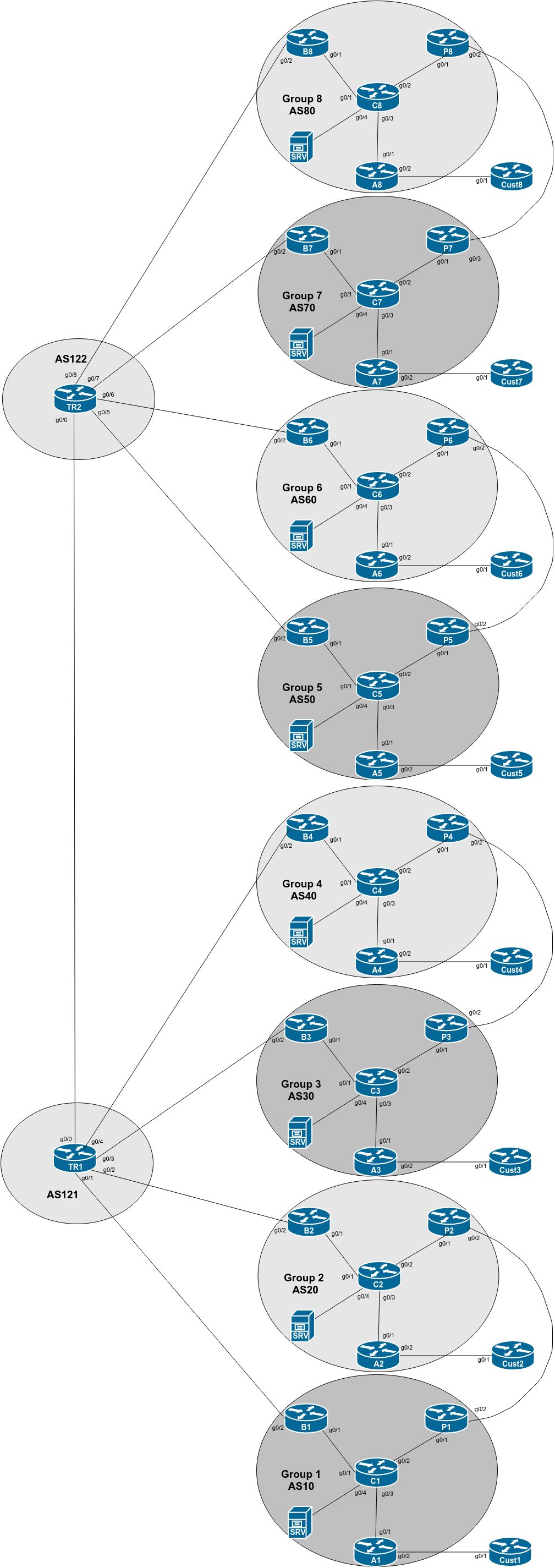
The purpose of this part of the lab is to set up private peering between adjacent autonomous systems. In our case, AS10 will private peer with AS20, AS30 with AS40, AS50 with AS60, and AS70 with AS80. We will use what we have learned so far to ensure that the adjacent ASNs only hear the routes they are meant to hear - a true private peering.
The lab topology has been enhanced according to the diagram below. We simply add in the peering links mentioned in the preamble.

Each group should now configure the private peering links as shown in the diagram.
Agree on which addresses should be used for the point-to-point links. Typically one group will contribute the IPv4 /31 and IPv6 /127 on the link. Look at the provided address plan for some spare point-to-point link addresses you can use.
interface GigabitEthernet 0/2
description Link to Group Y Peering Router
ip address <ptp-link> 255.255.255.254
no ip directed-broadcast
no ip redirects
no ip proxy-arp
ipv6 address <v6ptp-link>/127
ipv6 nd prefix default no-advertise
ipv6 nd ra suppress all
no shutdown
!Once the interfaces have been configured make sure that the links can be pinged on both IPv4 and IPv6 endpoints.
Do not configure IS-IS towards your private peer! They are not part of your autonomous system.
We now configure eBGP with the private peer. Don’t forget to filter what you hear from the private peer, and what you send to them. You should only accept their address blocks from them (they may send you more by mistake!), and you should only send prefixes you have originated!
First we confirm that we still have the prefix-lists for own our address blocks:
ip prefix-list ASX0-block permit 100.68.X.0/24
ipv6 prefix-list ASX0-v6block permit 2001:DB8:X::/48
!And then we set up the prefix lists for our private peer’s (Y) address blocks:
ip prefix-list ASY0-block permit 100.68.Y.0/24
ipv6 prefix-list ASY0-v6block permit 2001:DB8:Y::/48
!Here is a configuration sample, first for IPv4:
router bgp X0
!
address-family ipv4
neighbor <ptp-v4> remote-as Y0
neighbor <ptp-v4> description eBGP with ASY0
neighbor <ptp-v4> password BGPlab
neighbor <ptp-v4> prefix-list ASX0-block out
neighbor <ptp-v4> prefix-list ASY0-block in
neighbor <ptp-v4> activate
!and then for IPv6:
router bgp X0
!
address-family ipv6
neighbor <ptp-v6> remote-as Y0
neighbor <ptp-v6> description eBGP with ASY0
neighbor <ptp-v6> password BGPlab
neighbor <ptp-v6> prefix-list ASX0-v6block out
neighbor <ptp-v6> prefix-list ASY0-v6block in
neighbor <ptp-v6> activate
!Once this has been configured, you should now see your private peer originated routes coming from them, and you should be able to see your aggregate being sent to your private peer:
show ip bgp neigh <ptp-v4> routes
show bgp ipv6 uni neigh <ptp-v6> routesand to show what you are sending:
show ip bgp neigh <ptp-v4> advertised-routes
show bgp ipv6 uni neigh <ptp-v6> advertised-routes
Check on the Border, Core, Access and Peering Routers for what you now see in the BGP table.
What is the best path to your private peer? What does a traceroute tell you?
Hopefully you will see that the best path to your private peer will be via the private peering link. And the routes to the rest of the class will be via your upstream provider. If this is not the case, you will need to start doing some troubleshooting!
As with previous labs, try and ping your private peer’s routers from your routers. What do you see? If you ping your neighbour from your Peering Router, you might find that you have to send the pings sourced from the Loopback 0 interface of your Peering Router. How do you do that? Use the CLI help to find out.