
The purpose of this exercise is to create separate VLANs for different groups of users in each building. In a later exercise we will configure the core router so that each VLAN is using a different IP subnet.
This lab is a continuation from the Spanning Tree exercise and the lab setup is identical:

We now want to segment the network to separate network management traffic from end-user traffic (wired and wireless). Running one large flat network across the entire campus simply does not scale as was covered during the presentation. Each of these segments will be a separate subnet.
We need to take a structured approach with this migration. While we have the luxury of working in a lab for this workshop, on a campus network migration from a flat to a routed backbone needs care and planning.
The process will be this:
Create a VLAN for wired connections (called WIRED)
Create a VLAN for the wireless network (called WIFI)
Create a VLAN for device management (called NETMGMT)
Shut down VLAN1; VLAN1 is the Cisco default, has many well documented security risks for campus networks, and should never be used.
We will now create the VLANs described in the previous steps. As each VLAN is a different network, they need their own address subnet (IPv4 and IPv6). The Campus Core switch will route between each VLAN (so called L3-switch: an ethernet switch which has some L3 routing capability).
| Name | VLAN | IPv4 | IPv6 |
|---|---|---|---|
| Building 1 NETMGMT | 10 | 10.1.0.0/24 | 2001:DB8:X:10::/64 |
| Building 1 WIRED | 11 | 10.1.1.0/24 | 2001:DB8:X:11::/64 |
| Building 1 WIFI | 18 | 10.1.8.0/21 | 2001:DB8:X:18::/64 |
| Building 2 NETMGMT | 20 | 10.2.0.0/24 | 2001:DB8:X:20::/64 |
| Building 2 WIRED | 21 | 10.2.1.0/24 | 2001:DB8:X:21::/64 |
| Building 2 WIFI | 28 | 10.2.8.0/21 | 2001:DB8:X:28::/64 |
These IP addresses are also documented in the master IP address plan.
These two tables show the IP addresses which are assigned to the management interfaces of the core, distribution and edge switches. Replace the X and N in the configuration examples below with the appropriate numbers from these tables:
| Building 1 NETMGMT | VLAN | IPv4 | IPv6 |
|---|---|---|---|
| core1-campusX | 10 | 10.1.0.1/24 | 2001:DB8:X:10::1/64 |
| dist1-b1-campusX | 10 | 10.1.0.2/24 | 2001:DB8:X:10::2/64 |
| edge1-b1-campusX | 10 | 10.1.0.3/24 | 2001:DB8:X:10::3/64 |
| edge2-b1-campusX | 10 | 10.1.0.4/24 | 2001:DB8:X:10::4/64 |
| Building 2 NETMGMT | VLAN | IPv4 | IPv6 |
|---|---|---|---|
| core1-campusX | 20 | 10.2.0.1/24 | 2001:DB8:X:20::1/64 |
| dist1-b2-campusX | 20 | 10.2.0.2/24 | 2001:DB8:X:20::2/64 |
| edge1-b2-campusX | 20 | 10.2.0.3/24 | 2001:DB8:X:20::3/64 |
| edge2-b2-campusX | 20 | 10.2.0.4/24 | 2001:DB8:X:20::4/64 |
VTP (VLAN Trunking Protocol) is a proprietary Cisco technology that allows for dynamic VLAN provisioning. We will not use it here.
Disable VTP entirely:
vtp mode off(On older switches without vtp mode off, use vtp mode transparent instead)
Add the VLANs to the VLAN database on each switch and give them names to better identify them. If you don’t do this, the switches won’t know which VLANs are present in the network.
On the Core Switch:
vlan 10
name NETMGMT1
vlan 11
name WIRED1
vlan 18
name WIFI1
vlan 20
name NETMGMT2
vlan 21
name WIRED2
vlan 28
name WIFI2On Building 1 switches:
vlan 10
name NETMGMT1
vlan 11
name WIRED1
vlan 18
name WIFI1On Building 2 switches:
vlan 20
name NETMGMT2
vlan 21
name WIRED2
vlan 28
name WIFI2
Verify the Spanning Tree status:
show spanning-tree mstYou should see:
##### MST0 vlans mapped: 1-4094This means that all VLANs are being protected by the same spanning tree instance (MST0), and hence no additional configuration is required.
The Core switch connects to the Distribution switches in each building, which in turn connect to two Edge switches in each building. So that we can pass VLAN tags from switch to switch, we need to convert the interfaces which connect between the switches to trunk ports using 802.1Q encapsulation. (The Cisco default is for the interfaces to pass ethernet frames untagged.)
To set 802.1Q encapsulation on an interface (the default on most switches today1), the command used under the interface setting is switchport trunk encapsulation dot1q.
All switch ports are configured as access ports by default, so we need to convert the chosen port to a trunk port - to do this we use switchport mode trunk under the interface configuration. We also turn off Dynamic Trunking Protocol so that the port does not negotiate with its neighbour whether this is an access or a trunk port. This is the command switchport nonegotiate.
By default the switches will send all configured VLANs on all trunk interfaces. This will not scale for a large network, so we need to specifically list which VLANs are allowed on which trunks.
For example, the Core Switch should only allow VLANs 10, 11 and 18 towards Distribution Switch in Building 1. So we need to indicate on the interface which VLANs will be sent on the trunk port. For Building 1, the command we use is switchport trunk allowed vlan 10,11,18. And VLANs 20, 21 and 28 towards Distribution Switch in Building 2 - the command for those switches in Building 2 is switchport trunk allowed vlan 20,21,28.
Combining all the trunk settings we required, here is an example, on Distribution switch in Building1 in Campus1:
interface GigabitEthernet 1/0
description Trunk Link to edge1-b1-campus1
switchport trunk encapsulation dot1q
switchport mode trunk
switchport nonegotiate
switchport trunk allowed vlan 10,11,18
load-interval 30
!Reminder: Check the diagram to see which ports you need to modify - don’t just guess! Note that there are two links between the distribution and edge1 switch in each Building.
And don’t forget to put the descriptions on the interfaces and modify the default load interval from 5 minutes to 30 seconds!
We originally configured the switches so that we were using VLAN 1 to manage them (and provide end user access for the whole campus!). And the IPv4 address block we have used up to now was the entire 192.168.0.0/16 (for IPv6 we only used 2001:DB8:0:X::/64) as we had one large broadcast domain for the whole campus.
We need to move away from this now.
We cannot simply address the VLANs we created using a subnet of 192.168.0.0/16 while that entire address block is being used for VLAN 1; Cisco IOS does not allow overlapping subnets to be configured on routing devices (the core1-campusX switch will be routing traffic between the VLANs). So we are going to renumber the entire campus into another private address block, 10.0.0.0/8.
For this exercise we will simply remove the management IP addresses from VLAN 1 and set up new subnets on VLAN10 (NETMGMT for Building 1) and VLAN 20 (NETMGMT for Building 2)2.
The following diagram shows the VLAN structure we are now be building.
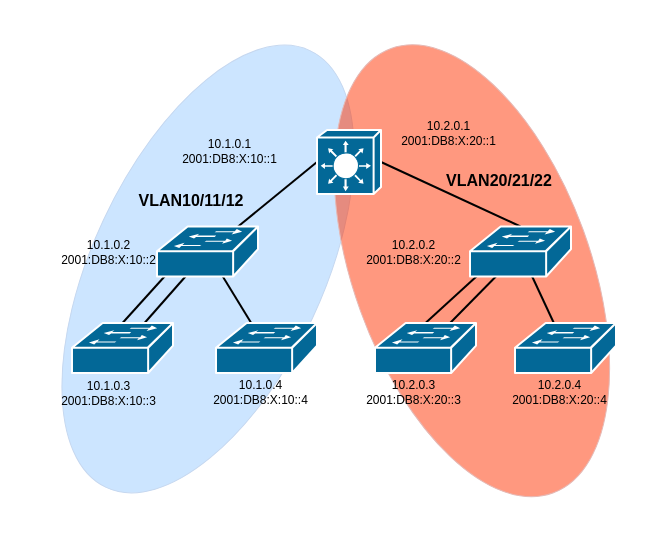
Remember that while we can delete an IPv4 address simply by doing no ip address, we have to type in the entire IPv6 address to delete it (because IPv6 allows multiple addresses per interfaces, unlike IPv4).
On the Core Switch:
interface vlan 1
no ip address
no ipv6 address 2001:DB8:0:X::2/64
shutdown
!
interface vlan 10
description Network Management VLAN Building 1
ip address 10.1.0.1 255.255.255.0
ipv6 address 2001:DB8:X:10::1/64
load-interval 30
no ip redirects
no ip proxy-arp
no shutdown
!
interface vlan 20
description Network Management VLAN Building 2
ip address 10.2.0.1 255.255.255.0
ipv6 address 2001:DB8:X:20::1/64
load-interval 30
no ip redirects
no ip proxy-arp
no shutdown
!In Building 1:
interface vlan 1
no ip address
no ipv6 address 2001:DB8:0:X::N/64
shutdown
!
interface vlan 10
description Network Management VLAN Building 1
ip address 10.1.0.N 255.255.255.0
ipv6 address 2001:DB8:X:10::N/64
load-interval 30
no ip redirects
no ip proxy-arp
no shutdown
!In Building 2:
interface vlan 1
no ip address
no ipv6 address 2001:DB8:0:X::N/64
shutdown
!
interface vlan 20
description Network Management VLAN Building 2
ip address 10.2.0.N 255.255.255.0
ipv6 address 2001:DB8:X:20::N/64
load-interval 30
no ip redirects
no ip proxy-arp
no shutdown
!Replace N with the actual number used in the address.
Carefully note the sequence in the configuration samples above. It is important to remove all IP addresses (both IPv4 and IPv6) from VLAN 1 and shut VLAN 1 down before anything is configured on the new management VLANs (VLAN 10 or VLAN 20).
Verify connectivity between switches. Can you ping?
Note: changing the Network Management VLANs is quite tricky to achieve by remotely accessing the switch - it is normally done by accessing the switch’s console port (like we are doing here in the lab). Cisco IOS requires VLAN 1 to be shutdown before any packets are moved on VLAN 10 or VLAN 20, so we can’t even use the trick of accessing the switch over IPv6 while the IPv4 address is being moved.
Now that the WIRED and WIFI VLANs have been created, we can designate 4 edge ports each for WIRED and WIFI VLAN access on the edge switches only (example is for Building 1). We also turn off Dynamic Trunking Protocol so that the port does not negotiate with its neighbour whether this is an access or a trunk port. As earlier, for the trunk ports, we use the command switchport nonegotiate:
interface range Gi1/0-3
description Access Port VLAN 11 WIRED
switchport mode access
switchport nonegotiate
switchport access vlan 11
load-interval 30
!
interface range Gi2/0-3
description Access Port VLAN 18 WIFI
switchport mode access
switchport nonegotiate
switchport access vlan 18
load-interval 30
!Verify which ports are members or trunks of each VLAN:
show vlan briefImagine that there are computers connected to the WIRED VLAN. Would they be able to ping the switch? Explain your response.
Now run the commands:
show interface description
show interface statusWhat do you see?
This is why it is important to make sure all interfaces have a description line configured - the above diagnostic command lets any operator see at one easy glance which switch interfaces are used for which function.
Trying pinging from switch to switch within your building. Ping the management interface addresses.
Can you ping any of the switches in the other building in your campus? What happens?
On modern Cisco switches (using IOS 15.0 onwards) the default is to use dot1q encapsulation (rather than the Cisco proprietary ISL). But we include the dot1q command in the configuration to enforce our requirements - the other options are isl and negotiate (where the switch will negotiate trunk encapsulation with its neighbour.↩︎
If doing this on a live network, removing the IP addressing and shutting down VLAN 1 will remove all Internet connectivity for all users connected to the switches - so this activity is best done when the network is unused, usually early in the mornings or at weekend, depending on when the campus is quietest.↩︎